The Evolution of Malware | From Simple Viruses to Advanced Persistent Threats (APTs)
Imagine a time when a computer virus was just a prank, displaying a cheeky message on your screen. Fast forward to today, and cyber threats have morphed into sophisticated operations capable of stealing sensitive data or even crippling entire organizations. Malware, short for malicious software, has evolved dramatically over the decades, adapting to new technologies and exploiting vulnerabilities in ways we could hardly have imagined. This blog post takes you on a journey through the history of malware, from its humble beginnings to the complex and stealthy Advanced Persistent Threats (APTs) of today. Whether you're a tech enthusiast or a beginner, we'll break it down in a way that's easy to grasp and engaging to read.
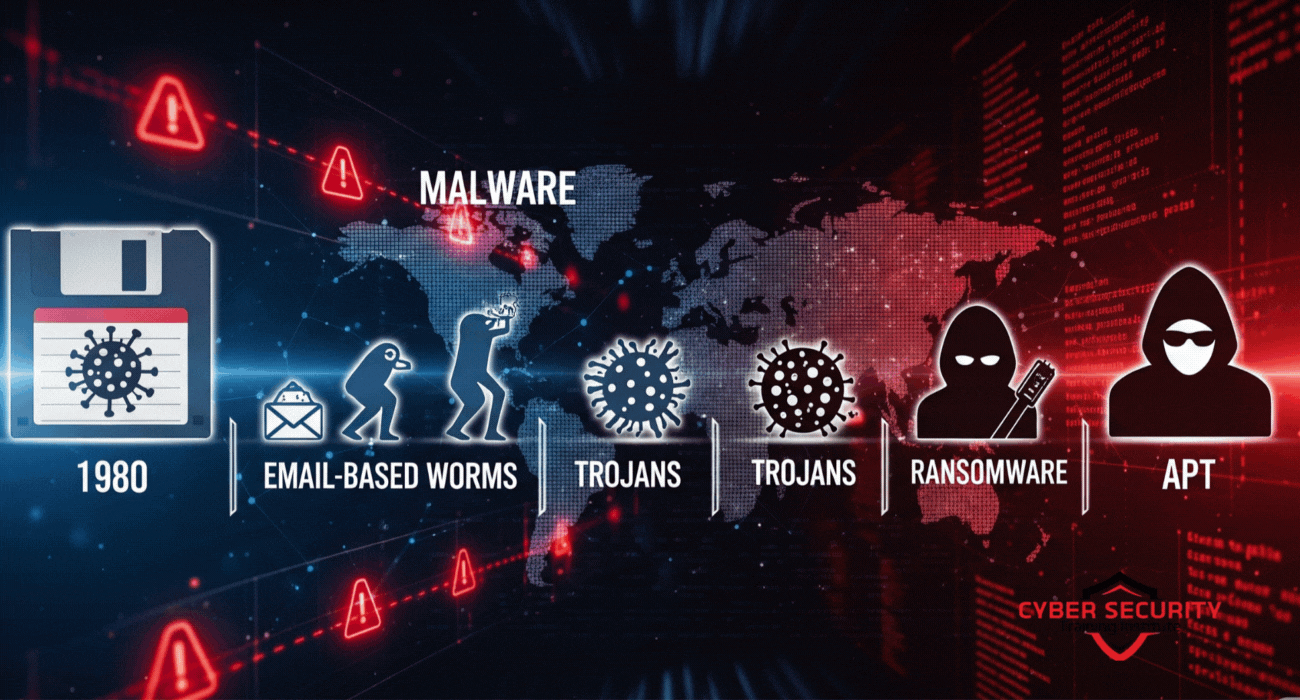
Table of Contents
- The Early Days of Malware: Simple Viruses
- The Rise of Worms and Trojans
- The Era of Modern Malware: Spyware, Ransomware, and Botnets
- The Emergence of Advanced Persistent Threats (APTs)
- Malware Evolution: A Comparison
- Protecting Against Modern Malware
- Conclusion
- Frequently Asked Questions (FAQs)
The Early Days of Malware: Simple Viruses
In the 1970s and 1980s, computers were clunky, and the internet was just a dream for most. Malware during this era was primitive, often created by curious programmers or pranksters. The first known computer virus, called the Creeper, appeared in 1971. It spread across ARPANET (an early version of the internet) and displayed a simple message: "I'M THE CREEPER: CATCH ME IF YOU CAN." It was harmless but proved that code could self-replicate and spread.
By the 1980s, viruses like the Brain virus (1986) emerged, targeting floppy disks, which were the main way to share data back then. These viruses would overwrite parts of the disk, slowing down systems or displaying annoying messages. Their goal was rarely malicious in the modern sense—most were experiments or jokes. However, they laid the groundwork for more dangerous threats by showing how code could spread without user consent.
The Rise of Worms and Trojans
As the internet grew in the 1990s, so did the opportunities for malware. This era saw the rise of worms and Trojans. Unlike viruses, which attach to files, worms are standalone programs that exploit network vulnerabilities to spread rapidly. The Morris Worm of 1988 was a wake-up call, infecting thousands of computers and causing significant disruptions. It wasn’t malicious by design, but its uncontrolled spread showed the potential for chaos.
Trojans, named after the Greek myth, disguise themselves as legitimate software. Users unknowingly install them, only to find their systems compromised. By the late 1990s, Trojans like Back Orifice allowed hackers to remotely control infected computers, marking a shift from pranks to espionage and data theft.
The Era of Modern Malware: Spyware, Ransomware, and Botnets
The 2000s brought a new level of sophistication to malware, driven by financial motives. Cybercriminals realized they could profit by stealing personal information or holding data hostage. This led to the rise of spyware, ransomware, and botnets.
- Spyware: Programs like Keyloggers secretly record keystrokes to steal passwords, credit card numbers, or other sensitive data. They often spread through malicious email attachments or shady downloads.
- Ransomware: This locks users out of their systems or encrypts their files, demanding payment for access. The WannaCry attack in 2017 affected over 200,000 computers worldwide, showing how devastating ransomware could be.
- Botnets: These are networks of infected computers controlled by hackers. Botnets like Conficker were used for everything from sending spam to launching large-scale attacks on websites.
The commercialization of malware meant cybercriminals were now organized, often operating in groups with clear profit-driven goals. Malware became a tool for cybercrime syndicates, not just lone hackers.
The Emergence of Advanced Persistent Threats (APTs)
By the 2010s, malware had evolved into something far more sinister: Advanced Persistent Threats (APTs). Unlike earlier malware, which often aimed for quick damage or profit, APTs are stealthy, long-term operations. They target specific organizations, such as governments, corporations, or critical infrastructure, with the goal of stealing sensitive data or causing strategic harm.
APTs are characterized by:
- Stealth: They use advanced techniques to avoid detection, such as mimicking legitimate software or exploiting previously unknown vulnerabilities (called zero-day exploits).
- Persistence: Attackers maintain access for months or even years, quietly collecting data.
- Customization: APTs are often tailored to their target, making them harder to detect with standard antivirus tools.
A famous example is Stuxnet (2010), a worm believed to be developed by state actors to sabotage Iran’s nuclear program. It targeted specific industrial systems, showing how malware could be weaponized for geopolitical purposes. Other APTs, like those linked to groups such as APT28 or Lazarus, have been tied to espionage and large-scale data breaches.
Malware Evolution: A Comparison
To understand how malware has changed, let’s compare its different stages:
| Era | Malware Type | Primary Goal | Spread Method | Example |
|---|---|---|---|---|
| 1970s–1980s | Viruses | Pranks, experiments | Floppy disks | Creeper, Brain |
| 1990s | Worms, Trojans | Disruption, remote control | Network vulnerabilities, downloads | Morris Worm, Back Orifice |
| 2000s | Spyware, Ransomware, Botnets | Financial gain | Emails, malicious websites | WannaCry, Conficker |
| 2010s–Present | APTs | Espionage, strategic harm | Targeted attacks, zero-day exploits | Stuxnet, APT28 |
Protecting Against Modern Malware
As malware has evolved, so have the ways to protect against it. Here are some practical steps anyone can take:
- Use Antivirus Software: Modern antivirus programs detect and remove most malware, including viruses, worms, and spyware.
- Keep Systems Updated: Regular updates patch vulnerabilities that malware exploits.
- Be Cautious Online: Avoid clicking suspicious links or downloading unverified files. Phishing emails are a common way malware spreads.
- Backup Data: Regular backups can save you from ransomware by ensuring you don’t lose critical files.
- Use Firewalls: A firewall acts as a barrier, blocking unauthorized access to your system.
- Educate Yourself: Learn to recognize phishing attempts and other common tactics used by cybercriminals.
For organizations facing APTs, advanced measures like intrusion detection systems, employee training, and regular security audits are essential. Staying proactive is key in a world where threats are constantly evolving.
Conclusion
The journey of malware from simple viruses to Advanced Persistent Threats mirrors the rapid advancement of technology itself. What began as playful experiments in the 1970s has grown into a complex landscape of cybercrime and espionage. Each era of malware—viruses, worms, ransomware, and APTs—has brought new challenges, forcing us to adapt and strengthen our defenses. By understanding this evolution, we can better appreciate the importance of cybersecurity in our daily lives. Whether you’re securing your personal devices or protecting an organization, staying informed and vigilant is the best defense against the ever-changing world of malware.
Frequently Asked Questions (FAQs)
What is malware?
Malware is software designed to harm or exploit computers, networks, or users, including viruses, worms, ransomware, and more.
How do viruses differ from worms?
Viruses attach to files and need user action to spread, while worms are standalone programs that spread automatically through networks.
What was the first computer virus?
The Creeper virus, created in 1971, was the first known computer virus, spreading across ARPANET with a harmless message.
What is a Trojan?
A Trojan is malware disguised as legitimate software, tricking users into installing it to gain unauthorized access.
What does ransomware do?
Ransomware locks or encrypts a user’s files, demanding payment (usually in cryptocurrency) to restore access.
What is a botnet?
A botnet is a network of infected computers controlled remotely by hackers to perform tasks like sending spam or attacking websites.
What are Advanced Persistent Threats (APTs)?
APTs are targeted, long-term cyberattacks aimed at stealing sensitive data or causing strategic harm, often by state-sponsored groups.
How did Stuxnet work?
Stuxnet was a worm that targeted industrial systems, specifically Iran’s nuclear program, by exploiting vulnerabilities to cause physical damage.
Can antivirus software stop all malware?
No, while antivirus software stops most malware, advanced threats like APTs may require additional security measures.
How do hackers spread malware?
Hackers use phishing emails, malicious downloads, infected websites, or network vulnerabilities to spread malware.
What is a zero-day exploit?
A zero-day exploit is a vulnerability in software that hackers use before developers can patch it.
How can I protect my computer from malware?
Use antivirus software, keep systems updated, avoid suspicious links, and back up data regularly.
Why do cybercriminals use malware?
Cybercriminals use malware for financial gain, espionage, disruption, or to gain unauthorized access to systems.
What is spyware?
Spyware secretly collects user data, like passwords or browsing habits, often for financial theft or espionage.
How do I know if my computer has malware?
Signs include slow performance, unusual pop-ups, unexpected crashes, or unauthorized account activity.
Can malware affect smartphones?
Yes, malware can infect smartphones through malicious apps, phishing links, or unsecured Wi-Fi networks.
What is phishing, and how is it related to malware?
Phishing is a tactic where hackers trick users into sharing sensitive information or downloading malware via fake emails or websites.
Are APTs only used by governments?
No, while often state-sponsored, APTs can also be used by organized crime groups targeting corporations or individuals.
How can businesses defend against APTs?
Businesses can use intrusion detection systems, employee training, regular audits, and advanced cybersecurity tools.
Will malware continue to evolve?
Yes, as technology advances, malware will adapt, likely incorporating AI and targeting new devices like IoT systems.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0















