What are the Cybersecurity Challenges in the Internet of Things (IoT)
The Internet of Things (IoT) is transforming our world, connecting everything from smart thermostats to wearable fitness trackers and even industrial machinery. These devices make life more convenient and efficient, but they also introduce significant cybersecurity risks. As billions of devices connect to the internet, they create new opportunities for cybercriminals to exploit vulnerabilities. This blog explores the key cybersecurity challenges in IoT, why they matter, and what can be done to address them. Whether you're a tech enthusiast or a beginner, this guide will break down the complexities in a simple, approachable way.
Table of Contents
- What is the Internet of Things (IoT)?
- Why Cybersecurity Matters in IoT
- Key Cybersecurity Challenges in IoT
- Solutions to IoT Cybersecurity Challenges
- The Future of IoT Security
- Conclusion
- Frequently Asked Questions (FAQs)
What is the Internet of Things (IoT)?
The Internet of Things refers to the network of physical devices embedded with sensors, software, and connectivity features that allow them to collect and exchange data over the internet. Think of your smart fridge that alerts you when you're low on milk or a fitness tracker that monitors your heart rate. IoT devices are everywhere—homes, offices, hospitals, factories, and even cities.
By 2025, experts estimate there will be over 75 billion IoT devices worldwide. This rapid growth is exciting but also raises concerns. Each connected device is a potential entry point for hackers, making cybersecurity a critical issue.
Why Cybersecurity Matters in IoT
IoT devices are often designed for convenience, not security. Many lack robust protections, making them easy targets for cyberattacks. A compromised IoT device can lead to serious consequences, such as:
- Data theft: Hackers can steal personal information like health records or financial details.
- Privacy breaches: Smart cameras or voice assistants can be hijacked to spy on users.
- Network attacks: A single vulnerable device can be a gateway to an entire network, putting businesses or homes at risk.
- Physical harm: Hacked medical devices or industrial systems could malfunction, causing real-world damage.
With IoT devices becoming integral to daily life, securing them is no longer optional—it’s a necessity.
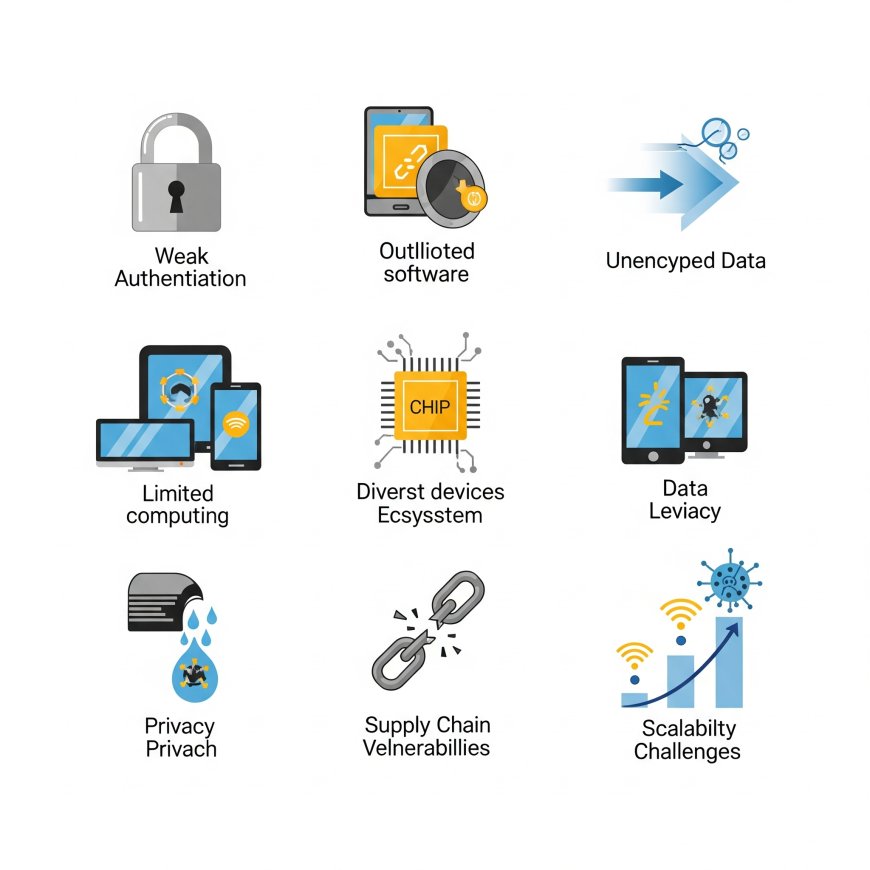
Key Cybersecurity Challenges in IoT
The unique nature of IoT devices creates several cybersecurity challenges. Below, we explore the most pressing issues.
1. Weak Authentication and Passwords
Many IoT devices come with default passwords like “admin” or “1234,” which users often fail to change. Hackers can easily guess these credentials to gain access. Additionally, some devices lack strong authentication methods, making it simple for unauthorized users to take control.
For example, in 2016, the Mirai botnet attack exploited weak passwords on IoT devices like cameras and routers, turning them into a massive network used to disrupt major websites.
2. Lack of Regular Software Updates
Unlike smartphones or computers, many IoT devices don’t receive regular software updates or patches. Manufacturers may prioritize new product releases over maintaining older devices, leaving them vulnerable to known exploits.
Without updates, a device’s software can become outdated, making it an easy target for hackers who exploit known vulnerabilities.
3. Insecure Data Transmission
IoT devices constantly send and receive data, often over unsecured networks. If this data isn’t encrypted, hackers can intercept it. For instance, a smart thermostat might send unencrypted temperature data, which seems harmless but could reveal when a home is unoccupied.
Unencrypted communication is a significant risk, especially for devices handling sensitive information like medical or financial data.
4. Limited Computing Power
IoT devices are often small and designed to be energy-efficient, which limits their processing power. This makes it challenging to implement advanced security features like strong encryption or complex authentication protocols.
For example, a smart light bulb can’t run the same security software as a laptop, leaving it more exposed to attacks.
5. Diverse Device Ecosystem
The IoT landscape includes devices from countless manufacturers, each with different operating systems, protocols, and standards. This diversity makes it hard to create universal security solutions. A security patch for one brand’s smart lock might not work for another’s.
This fragmentation complicates efforts to secure entire IoT networks, as each device may have unique vulnerabilities.
6. Privacy Concerns
IoT devices often collect personal data, such as location, health metrics, or daily routines. If not properly secured, this data can be misused. For example, a hacked smart speaker could record private conversations, leading to serious privacy violations.
Consumers may not even realize how much data their devices collect, making it critical to prioritize privacy protections.
7. Supply Chain Vulnerabilities
IoT devices often involve complex supply chains, with components sourced from multiple vendors. A single weak link, like a compromised chip or pre-installed malware, can jeopardize the entire device.
In 2020, researchers discovered vulnerabilities in IoT device supply chains, where malicious code was embedded during manufacturing, highlighting this growing risk.
8. Scalability Challenges
As the number of IoT devices grows, so does the challenge of securing them. Managing security for millions or billions of devices requires significant resources, coordination, and expertise—something many organizations struggle to achieve.
Large-scale IoT deployments, like smart cities, amplify these challenges, as a single breach could affect entire systems.
Solutions to IoT Cybersecurity Challenges
Addressing IoT cybersecurity requires a multi-faceted approach involving manufacturers, users, and policymakers. Here are some practical solutions:
1. Stronger Authentication
Manufacturers should enforce unique, complex default passwords and support multi-factor authentication (MFA). For example, requiring a password and a one-time code sent to a user’s phone can significantly reduce unauthorized access.
Users should also change default passwords immediately and use password managers to create strong credentials.
2. Regular Software Updates
Manufacturers must commit to providing regular firmware and software updates to patch vulnerabilities. Devices should support automatic updates to ensure users stay protected without manual effort.
Consumers should check for updates regularly and avoid using devices from brands that don’t provide ongoing support.
3. End-to-End Encryption
Data transmitted by IoT devices should be encrypted using strong protocols like AES-256. This ensures that even if data is intercepted, it’s unreadable to hackers.
Manufacturers should prioritize secure communication standards, and users should verify that their devices use encryption.
4. Designing Secure Devices
Security should be built into IoT devices from the ground up, a concept known as “security by design.” This includes using secure hardware, minimizing data collection, and ensuring devices can handle basic security tasks despite limited processing power.
For example, chipmakers are developing lightweight encryption algorithms tailored for low-power IoT devices.
5. Standardizing IoT Security
Industry-wide standards can help address the diversity of IoT devices. Organizations like the Internet Engineering Task Force (IETF) are working on protocols to ensure consistent security practices across manufacturers.
Governments can also enforce regulations requiring minimum security standards for IoT devices.
6. Educating Users
Many IoT security issues stem from user error, like failing to change default passwords. Public awareness campaigns and user-friendly guides can empower consumers to secure their devices.
Manufacturers should include clear instructions on securing devices during setup.
7. Securing the Supply Chain
Manufacturers must vet suppliers and implement strict quality controls to prevent compromised components. Blockchain technology is being explored to track and verify the integrity of IoT supply chains.
8. Network Segmentation
Users can reduce risks by separating IoT devices from critical systems. For example, placing smart home devices on a separate Wi-Fi network ensures that a compromised device doesn’t grant access to sensitive data on your laptop or phone.
The Future of IoT Security
As IoT continues to grow, so will the efforts to secure it. Emerging technologies like artificial intelligence (AI) and machine learning (ML) are being used to detect and respond to threats in real-time. For example, AI can analyze patterns in IoT device behavior to identify anomalies that suggest a hack.
Quantum computing, though still in its infancy, could revolutionize encryption, making IoT communications even more secure. Meanwhile, governments and industries are collaborating on regulations and standards to ensure IoT devices meet minimum security requirements.
However, the responsibility doesn’t lie solely with manufacturers or policymakers. Consumers must stay informed and take proactive steps to protect their devices. The future of IoT security depends on collective action from all stakeholders.
Conclusion
The Internet of Things is reshaping how we live and work, but its rapid growth comes with significant cybersecurity challenges. Weak passwords, outdated software, unencrypted data, and diverse device ecosystems create vulnerabilities that hackers can exploit. By adopting stronger authentication, regular updates, encryption, and industry standards, we can mitigate these risks. Users also play a crucial role by staying informed and securing their devices. As technology evolves, so will the solutions to keep IoT safe, ensuring we can enjoy its benefits without compromising security.
Frequently Asked Questions (FAQs)
What is the Internet of Things (IoT)?
IoT refers to devices connected to the internet that collect and share data, like smart thermostats or fitness trackers.
Why is IoT security important?
IoT security prevents data theft, privacy breaches, and network attacks that can occur when devices are compromised.
What are common IoT cybersecurity risks?
Risks include weak passwords, unencrypted data, outdated software, and supply chain vulnerabilities.
How do hackers target IoT devices?
Hackers exploit weak passwords, unpatched software, or unsecured networks to gain access to devices.
Can IoT devices be hacked easily?
Yes, especially if they have default passwords or lack encryption and updates.
What is the Mirai botnet?
Mirai was a 2016 cyberattack that used compromised IoT devices to disrupt major websites.
How can I secure my IoT devices?
Change default passwords, enable updates, use encryption, and place devices on a separate network.
What is security by design?
It’s the practice of building security into devices from the start, not as an afterthought.
Why don’t IoT devices get regular updates?
Some manufacturers prioritize new products over maintaining older devices, leaving them vulnerable.
What is encryption in IoT?
Encryption scrambles data so only authorized users can read it, protecting it from hackers.
Can IoT devices compromise my privacy?
Yes, hacked devices like smart cameras can leak personal data or record private moments.
What is multi-factor authentication (MFA)?
MFA requires multiple verification steps, like a password and a code, to access a device.
Why is the IoT device ecosystem so diverse?
Different manufacturers use unique systems and protocols, creating a fragmented landscape.
How does network segmentation help?
It isolates IoT devices, limiting damage if one is hacked.
What role does AI play in IoT security?
AI detects unusual device behavior, helping identify and stop threats quickly.
Are there laws for IoT security?
Some countries are introducing regulations, but global standards are still developing.
What is a supply chain attack?
It’s when hackers compromise a device through its manufacturing or supply process.
Can IoT devices cause physical harm?
Yes, hacked medical or industrial devices could malfunction, causing real-world damage.
How can manufacturers improve IoT security?
They can use strong authentication, encryption, regular updates, and secure supply chains.
What’s the future of IoT security?
AI, quantum computing, and stricter regulations will likely enhance IoT security.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0















