Intrusion Detection Systems (IDS) | What They Are, Types, How They Work, and How They Protect Your Network from Cyber Threats
Intrusion Detection Systems (IDS) play a vital role in modern cybersecurity by monitoring network traffic to detect and respond to unauthorized or suspicious activity. These systems serve as a digital surveillance layer, identifying possible threats like malware, port scanning, brute-force attacks, and insider misuse. This blog explains what IDS is, how it works, the difference between signature-based and anomaly-based detection, and how IDS fits into enterprise and personal security strategies. Whether you're a cybersecurity professional or a tech-savvy user, understanding IDS is essential for protecting your digital environment.

Table of Contents
- Introduction
- What is an Intrusion Detection System?
- Types of Intrusion Detection Systems
- How Does an IDS Work?
- Benefits of Implementing an IDS
- Challenges and Limitations of IDS
- IDS vs. IPS: What’s the Difference?
- Real-World Use Cases of IDS
- The Future of Intrusion Detection Systems
- Frequently Asked Questions (FAQ)
- Conclusion
Introduction
In today’s hyper-connected world, cyber threats are evolving at an unprecedented pace. From sophisticated malware to insider threats, organizations face constant risks to their sensitive data and critical systems. Enter the Intrusion Detection System (IDS), a cornerstone of modern cybersecurity that acts as a vigilant sentinel, monitoring networks and systems for suspicious activities. This blog explores the intricacies of IDS, their types, functionalities, benefits, and future trends, providing a comprehensive guide for anyone looking to bolster their cybersecurity defenses.
What is an Intrusion Detection System?
An Intrusion Detection System (IDS) is a security tool designed to monitor network traffic or system activities for malicious behavior or policy violations. When an anomaly or threat is detected, the IDS generates alerts to notify administrators, enabling rapid response to potential incidents. Unlike firewalls, which primarily block unauthorized access, IDS focuses on identifying and reporting threats, making it an essential component of a layered security strategy.
IDS can be deployed in various environments, including enterprise networks, cloud infrastructures, and even individual devices, ensuring comprehensive threat detection across diverse systems.
Types of Intrusion Detection Systems
IDS solutions come in various forms, each tailored to specific use cases and environments. Below are the primary types:
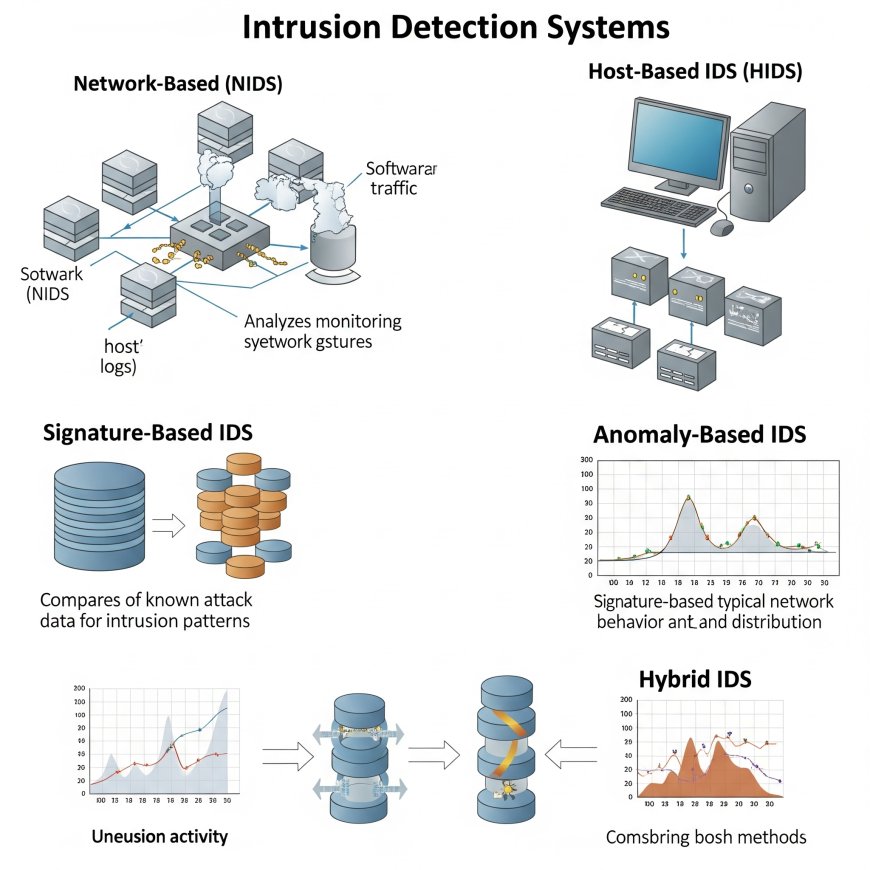
1. Network-Based IDS (NIDS)
Network-based IDS monitors network traffic for suspicious patterns, such as unusual packet flows or known attack signatures. Deployed at strategic points like routers or gateways, NIDS analyzes data packets to detect threats like Distributed Denial-of-Service (DDoS) attacks or unauthorized access attempts.
2. Host-Based IDS (HIDS)
Host-based IDS operates on individual devices or servers, monitoring system logs, file integrity, and user activities. HIDS is particularly effective for detecting insider threats or malware that may bypass network-level defenses.
3. Signature-Based IDS
Signature-based IDS relies on a database of known attack patterns or "signatures" to identify threats. While highly effective against known attacks, it may struggle with zero-day exploits or previously unseen threats.
4. Anomaly-Based IDS
Anomaly-based IDS uses machine learning or statistical models to establish a baseline of normal behavior. Any deviation from this baseline triggers an alert, making it ideal for detecting novel or sophisticated attacks.
5. Hybrid IDS
Hybrid IDS combines multiple detection methods (e.g., signature-based and anomaly-based) to provide comprehensive threat coverage, balancing accuracy and adaptability.
How Does an IDS Work?
An IDS operates by analyzing data from various sources, such as network packets, system logs, or application activities. The process typically involves the following steps:
- Data Collection: The IDS gathers data from network traffic, system logs, or device activities.
- Analysis: Using predefined rules, signatures, or machine learning algorithms, the IDS evaluates the data for signs of malicious activity.
- Detection: If a potential threat is identified, the IDS categorizes it based on severity and type (e.g., malware, unauthorized access).
- Alerting: The IDS generates alerts or logs the incident, notifying administrators via email, dashboards, or Security Information and Event Management (SIEM) systems.
- Response (Optional): While IDS primarily focuses on detection, some systems integrate with Intrusion Prevention Systems (IPS) to take automated actions, such as blocking malicious traffic.
Modern IDS solutions often leverage artificial intelligence (AI) and machine learning to improve detection accuracy and reduce false positives, adapting to evolving threats in real-time.
Benefits of Implementing an IDS
Deploying an IDS offers numerous advantages for organizations seeking to enhance their cybersecurity posture:
- Proactive Threat Detection: Identifies potential threats before they cause significant damage.
- Compliance Support: Helps organizations meet regulatory requirements, such as GDPR, HIPAA, or PCI-DSS, by monitoring and logging security events.
- Improved Incident Response: Provides detailed alerts and logs, enabling faster investigation and mitigation of incidents.
- Enhanced Visibility: Offers insights into network and system activities, helping administrators identify vulnerabilities.
- Scalability: Can be deployed across diverse environments, from small businesses to large enterprises.
Challenges and Limitations of IDS
While IDS is a powerful tool, it’s not without challenges:
- False Positives: Anomaly-based IDS may generate alerts for benign activities, overwhelming security teams.
- Zero-Day Attacks: Signature-based IDS struggles to detect new or unknown threats.
- Resource Intensive: Continuous monitoring can strain system resources, especially in large networks.
- Complex Configuration: Proper setup and tuning require expertise to avoid misconfigurations.
- Limited Prevention: IDS focuses on detection, not prevention, requiring integration with other tools like IPS for comprehensive protection.
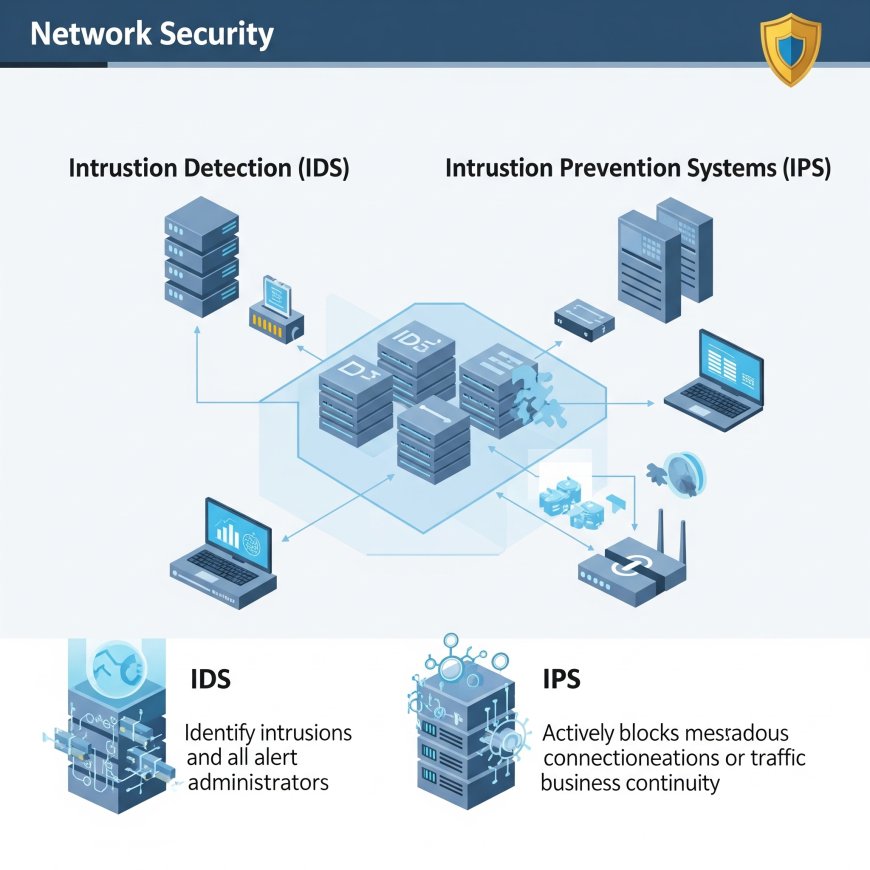
IDS vs. IPS: What’s the Difference?
While IDS and Intrusion Prevention Systems (IPS) are often mentioned together, they serve distinct purposes:
- IDS: Monitors and alerts on suspicious activities but does not take action to block threats.
- IPS: Actively blocks or mitigates threats by filtering traffic or modifying access controls.
Many modern security solutions combine IDS and IPS functionalities, offering both detection and prevention capabilities for a robust defense.
Real-World Use Cases of IDS
IDS is deployed across various industries to address specific security challenges:
- Financial Sector: Detects unauthorized access to banking systems or fraudulent transactions.
- Healthcare: Protects sensitive patient data from breaches, ensuring HIPAA compliance.
- E-commerce: Monitors for DDoS attacks or payment system vulnerabilities.
- Government: Safeguards critical infrastructure from state-sponsored cyberattacks.
- Education: Prevents unauthorized access to student records or institutional networks.
The Future of Intrusion Detection Systems
As cyber threats grow in complexity, IDS solutions are evolving to keep pace. Key trends include:
- AI and Machine Learning: Enhancing anomaly detection and reducing false positives.
- Cloud-Native IDS: Tailored for cloud environments, offering scalability and flexibility.
- Integration with SOAR: Combining IDS with Security Orchestration, Automation, and Response (SOAR) platforms for streamlined incident response.
- Zero Trust Architecture: Incorporating IDS into zero trust models to verify all network activities.
- IoT Security: Adapting IDS to monitor and protect the growing number of IoT devices.
Conclusion
Intrusion Detection Systems are indispensable in the fight against cyber threats, offering proactive monitoring and rapid threat detection. By understanding the types, functionalities, and challenges of IDS, organizations can make informed decisions to strengthen their security posture. As cyber threats continue to evolve, IDS solutions are adapting with AI, cloud compatibility, and integration with broader security frameworks, ensuring they remain a vital tool for safeguarding digital assets. Whether you’re a small business or a global enterprise, investing in an IDS is a critical step toward a secure and resilient future.
Frequently Asked Questions (FAQ)
What is the primary function of an IDS?
An Intrusion Detection System (IDS) monitors network or system activity for malicious actions or policy violations.
How does an IDS differ from a firewall?
A firewall controls incoming and outgoing traffic based on rules, while an IDS analyzes traffic to detect threats and alert administrators.
Can an IDS prevent cyberattacks?
Most IDS tools are passive and only detect and alert. However, when combined with prevention systems (like IPS), some attacks can be blocked.
What is the difference between NIDS and HIDS?
NIDS (Network IDS) monitors traffic on a network, while HIDS (Host IDS) monitors activities on a specific device or host.
What are signature-based and anomaly-based IDS?
Signature-based IDS detects known threats using predefined patterns, while anomaly-based IDS detects unusual behavior that may indicate unknown threats.
Can IDS detect zero-day attacks?
Anomaly-based IDS has the potential to detect zero-day attacks by identifying abnormal activity, even if no known signature exists.
Is IDS suitable for small businesses?
Yes, many lightweight and open-source IDS solutions are ideal for small businesses seeking affordable network security.
How does AI improve IDS performance?
AI enhances IDS by analyzing large datasets, reducing false positives, and adapting to new threat patterns using machine learning.
What are false positives in IDS?
False positives occur when legitimate activity is incorrectly identified as malicious, potentially causing unnecessary alerts.
Can IDS be used in cloud environments?
Yes, IDS tools are available for cloud infrastructures and can monitor virtual networks and cloud workloads.
How does IDS support compliance?
IDS helps organizations meet cybersecurity compliance standards like PCI-DSS, HIPAA, and ISO 27001 by providing visibility and audit trails.
What is a hybrid IDS?
A hybrid IDS combines signature-based and anomaly-based methods to increase accuracy and reduce detection gaps.
How resource-intensive is an IDS?
Resource usage depends on the type and configuration. NIDS may require more bandwidth and processing power compared to HIDS.
Can IDS protect against insider threats?
Yes, HIDS can detect unauthorized activities by insiders on specific endpoints or servers.
What is the role of IDS in a zero trust architecture?
In zero trust models, IDS provides continuous monitoring and alerting, ensuring no implicit trust and detecting suspicious activity at every layer.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0

















