What are the types of Cyber Threats | A Deep Dive into Attack Vectors
In today’s digital age, where our lives are intertwined with technology, the risk of cyber threats looms larger than ever. From personal data breaches to massive corporate hacks, cybercriminals are constantly finding new ways to exploit vulnerabilities. But what exactly are these cyber threats, and how do they work? This blog post takes a deep dive into the various types of cyber threats, breaking down their attack vectors in a way that’s easy to understand, even if you’re new to the world of cybersecurity. Whether you’re a business owner, an employee, or just someone who uses the internet, knowing about these threats can help you stay one step ahead of the bad guys.
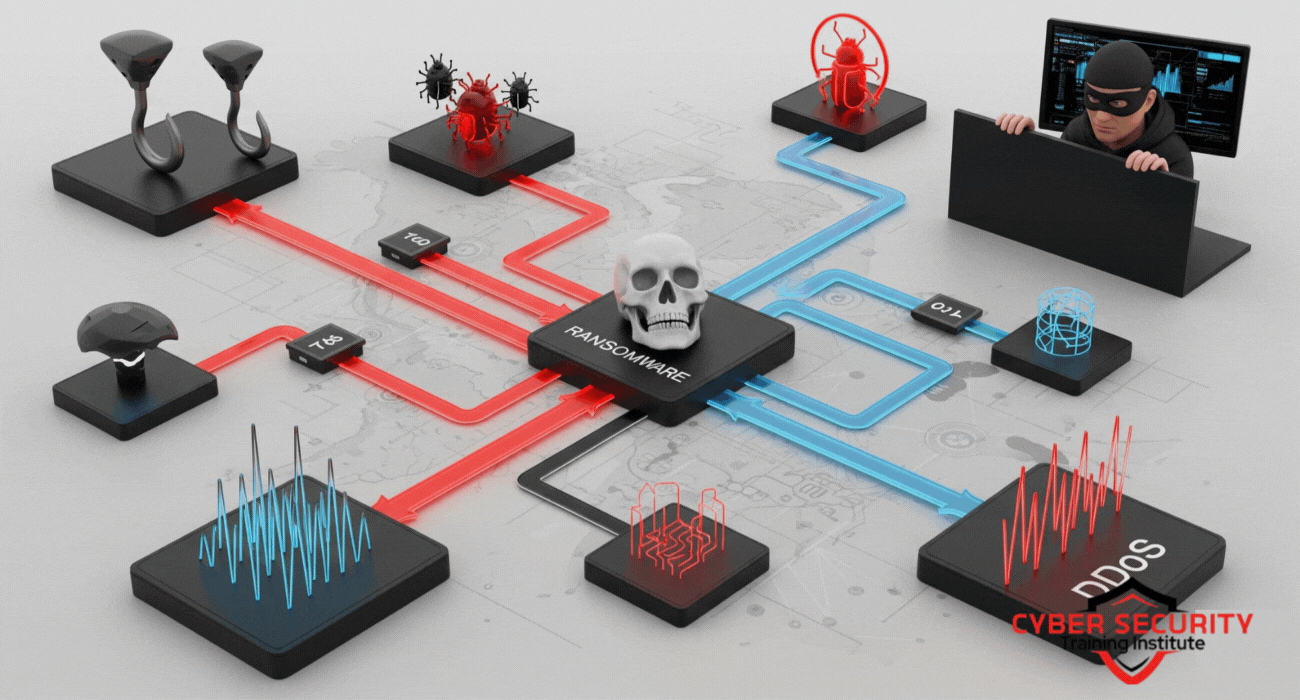
Table of Contents
- What Are Cyber Threats?
- Common Types of Cyber Threats
- Understanding Attack Vectors
- Comparison of Major Cyber Threats
- Protecting Yourself from Cyber Threats
- Conclusion
- Frequently Asked Questions (FAQs)
What Are Cyber Threats?
A cyber threat is any malicious attempt to disrupt, damage, or gain unauthorized access to a computer system, network, or device. These threats come in many forms, targeting individuals, businesses, and even governments. The goal of cybercriminals is often to steal sensitive information, disrupt operations, or extort money. Understanding these threats is the first step to protecting yourself.
Cyber threats are constantly evolving as technology advances. What was once a simple virus sent via email has now transformed into sophisticated attacks that can bypass even the most robust defenses. Let’s explore some of the most common types of cyber threats and how they work.
Common Types of Cyber Threats
Below, we’ll break down the most prevalent cyber threats, explaining what they are and how they operate in simple terms.
Malware
Malware, short for malicious software, is a broad term for programs designed to harm or exploit a device. Common types of malware include:
- Viruses: These attach themselves to legitimate programs and spread when the program is run, potentially corrupting files or slowing down systems.
- Worms: Unlike viruses, worms spread on their own across networks, often exploiting security flaws to infect multiple devices.
- Ransomware: This locks your files or device and demands a ransom to regain access. For example, the WannaCry attack in 2017 encrypted data on thousands of computers worldwide.
- Spyware: This secretly monitors your activities, such as tracking your browsing habits or stealing passwords.
- Trojans: Disguised as harmless software, trojans trick users into installing them, only to create backdoors for hackers.
Phishing Attacks
Phishing is when cybercriminals send fraudulent emails, text messages, or other communications pretending to be from a trusted source. The goal is to trick you into sharing sensitive information, like login credentials or credit card details, or clicking malicious links. For instance, you might receive an email that looks like it’s from your bank, asking you to “verify” your account by entering your password.
Denial-of-Service (DoS) Attacks
A Denial-of-Service attack overwhelms a system, server, or network with traffic, making it unavailable to users. Imagine a highway jammed with too many cars—legitimate users can’t get through. Distributed Denial-of-Service (DDoS) attacks are a more complex version, using multiple devices to flood the target.
Man-in-the-Middle (MitM) Attacks
In a MitM attack, a hacker secretly intercepts communication between two parties. For example, if you’re using unsecured public Wi-Fi, a cybercriminal could intercept your data, like login details, as you send it to a website.
Social Engineering
Social engineering exploits human psychology rather than technical vulnerabilities. Attackers manipulate people into divulging confidential information or performing actions that compromise security. Phishing is a type of social engineering, but other forms include pretexting (creating a fabricated scenario to gain trust) or baiting (offering something enticing, like free software, that’s actually malicious).
SQL Injection
SQL injection targets websites by inserting malicious code into input fields, like a login form. If the website’s database isn’t secure, the attacker can manipulate it to access sensitive data, such as user credentials. This is common in poorly designed websites or apps.
Zero-Day Exploits
A zero-day exploit targets a software vulnerability that the developer doesn’t yet know about (hence “zero days” to fix it). Hackers exploit these flaws before a patch is available, making them particularly dangerous.
Understanding Attack Vectors
An attack vector is the method or pathway a cybercriminal uses to deliver a threat. Think of it as the “door” they use to break into your digital house. Common attack vectors include:
- Email: Phishing emails are one of the most common attack vectors, delivering malware or tricking users into sharing sensitive information.
- Websites: Visiting a compromised website can automatically download malware or prompt you to enter personal details.
- Networks: Unsecured Wi-Fi or poorly configured networks can allow hackers to intercept data or launch attacks like DDoS.
- Removable Media: USB drives or external hard drives can carry malware that activates when plugged into a device.
- Human Error: Mistakes like weak passwords or falling for social engineering are exploited as attack vectors.
By understanding these pathways, you can better protect yourself by securing potential entry points.
Comparison of Major Cyber Threats
| Threat Type | Primary Goal | Common Attack Vector | Impact |
|---|---|---|---|
| Malware | Damage, steal data, or extort | Email, websites, USB drives | Data loss, system damage, ransom demands |
| Phishing | Steal credentials or data | Email, text messages | Identity theft, financial loss |
| DoS/DDoS | Disrupt services | Networks | Website downtime, loss of revenue |
| MitM | Intercept data | Unsecured Wi-Fi | Data theft, privacy violation |
| SQL Injection | Access database | Websites | Data breach, system compromise |
| Zero-Day | Exploit unknown flaws | Software vulnerabilities | Widespread damage, hard to detect |
Protecting Yourself from Cyber Threats
While cyber threats are scary, there are practical steps you can take to stay safe:
- Use Strong Passwords: Create complex passwords and use a password manager to keep track of them.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of verification, like a code sent to your phone.
- Update Software Regularly: Keep your operating system, apps, and antivirus software up to date to patch vulnerabilities.
- Be Cautious with Emails: Don’t click links or download attachments from unknown or suspicious emails.
- Use Secure Networks: Avoid public Wi-Fi unless you’re using a virtual private network (VPN).
- Backup Your Data: Regularly back up important files to an external drive or cloud service to protect against ransomware.
- Educate Yourself: Learn to recognize phishing attempts and other social engineering tactics.
By adopting these habits, you can significantly reduce your risk of falling victim to cyber threats.
Conclusion
Cyber threats are a growing concern in our connected world, but understanding them is the first step to staying safe. From malware and phishing to DoS attacks and zero-day exploits, cybercriminals use a variety of tactics to exploit vulnerabilities. By recognizing these threats and their attack vectors, you can take proactive steps to protect your data and devices. Whether it’s using strong passwords, staying cautious with emails, or keeping your software updated, small actions can make a big difference. Stay informed, stay vigilant, and keep cybersecurity first in this digital age.
Frequently Asked Questions (FAQs)
What is a cyber threat?
A cyber threat is any malicious attempt to disrupt, damage, or gain unauthorized access to a computer system, network, or device.
What is malware?
Malware is malicious software designed to harm or exploit devices, including viruses, worms, ransomware, spyware, and trojans.
How does phishing work?
Phishing involves cybercriminals sending fake emails or messages pretending to be from trusted sources to trick users into sharing sensitive information.
What is ransomware?
Ransomware locks your files or device and demands payment to regain access.
What is a DoS attack?
A Denial-of-Service attack overwhelms a system with traffic to make it unavailable to users.
What is a DDoS attack?
A Distributed Denial-of-Service attack uses multiple devices to flood a target, amplifying the disruption.
What is a Man-in-the-Middle attack?
A MitM attack involves a hacker intercepting communication between two parties to steal data.
What is social engineering?
Social engineering manipulates people into sharing confidential information or performing actions that compromise security.
What is SQL injection?
SQL injection involves inserting malicious code into a website’s input fields to manipulate its database.
What is a zero-day exploit?
A zero-day exploit targets a software vulnerability before the developer knows about it or releases a fix.
What is an attack vector?
An attack vector is the method or pathway a cybercriminal uses to deliver a threat, like email or unsecured networks.
How can I protect myself from malware?
Use antivirus software, avoid suspicious downloads, and keep your system updated.
How can I spot a phishing email?
Look for suspicious senders, urgent language, or requests for personal information. Verify the source before clicking links.
Why are strong passwords important?
Strong passwords make it harder for hackers to guess or crack your credentials.
What is two-factor authentication?
Two-factor authentication requires a second form of verification, like a code sent to your phone, in addition to your password.
Can public Wi-Fi be dangerous?
Yes, unsecured public Wi-Fi can allow hackers to intercept your data. Use a VPN for safety.
What should I do if I’m hit by ransomware?
Disconnect the device from the internet, report to authorities, and restore from a backup if possible. Avoid paying the ransom.
How do I know if a website is safe?
Check for “https://” in the URL, a padlock icon, and avoid sites with poor design or suspicious pop-ups.
What is a VPN?
A Virtual Private Network encrypts your internet connection, making it harder for hackers to intercept your data.
How often should I back up my data?
Back up important files regularly, ideally weekly or after major changes, to protect against data loss.
What's Your Reaction?
 Like
0
Like
0
 Dislike
0
Dislike
0
 Love
0
Love
0
 Funny
0
Funny
0
 Angry
0
Angry
0
 Sad
0
Sad
0
 Wow
0
Wow
0














